Learn how to build zero-trust cloud infrastructure using OpenStack and Atmosphere. Discover security-by-default practices for enterprise private cloud in 2026.
The traditional "castle and moat" approach to security—where everything inside the network is trusted—is no longer viable. With distributed workloads, remote teams, and increasingly sophisticated threats, the perimeter has dissolved. In 2026, enterprises aren't asking if they should adopt zero-trust principles; they're asking how.
At VEXXHOST, security-by-default is a core investment priority this year (it has always been). We believe security shouldn't be an afterthought or an add-on—it should be baked into your cloud infrastructure from day one. In this post, we'll explore how to build zero-trust cloud infrastructure using OpenStack and our Atmosphere platform.
What Is Zero-Trust Architecture?
Zero-trust operates on a simple principle: never trust, always verify. Every user, device, and workload must continuously prove its identity and authorization—regardless of where it sits in your network.
The core tenets include:
- Verify explicitly: Authenticate and authorize based on all available data points (identity, location, device health, workload context)
- Least-privilege access: Limit user and service permissions to only what's necessary
- Assume breach: Design systems as if attackers are already inside; minimize blast radius through micro-segmentation
For cloud infrastructure, this means rethinking how identity, networking, and access controls work together.
For a comprehensive framework on zero-trust principles, refer to NIST Special Publication 800-207, Zero Trust Architecture, the foundational government standard for enterprise ZTA implementation.
Why Private Cloud Is the Natural Fit for Zero-Trust
Public cloud providers offer security tools, but implementing true zero-trust often means navigating a patchwork of services, proprietary configurations, and opaque networking layers. You're trusting the provider's implementation without full visibility.
Private cloud built on OpenStack offers distinct advantages:
Full Control Over the Security Stack
You own every layer, from hypervisor to API endpoint. There's no black box. You can audit, customize, and harden each component to meet your specific threat model.
Network Transparency
OpenStack's Neutron networking gives you complete visibility into traffic flows. You can implement micro-segmentation, define security groups with precision, and inspect east-west traffic that would be invisible in shared public cloud environments.
Data Sovereignty
With private cloud, your data stays exactly where you mandate—critical for organizations navigating GDPR, HIPAA, SOC 2, or industry-specific regulations.
No Shared Tenancy Risk
Multi-tenant public clouds introduce inherent risks. Side-channel attacks, noisy neighbors, and shared infrastructure vulnerabilities disappear when you control the hardware.
How Atmosphere Implements Security-by-Default
Atmosphere, our OpenStack-based cloud platform, is designed with security built into its foundation—not bolted on later. Here's how:
Integrated Identity Management
Authentication is the front door to zero-trust, and Atmosphere gives you enterprise-grade options out of the box:
- Keycloak Integration: Centralized identity and access management with support for multi-factor authentication (MFA), session management, and fine-grained authorization policies
- LDAP/Active Directory: Seamlessly connect to your existing directory services—no need to maintain separate user databases
- SAML 2.0 & OpenID Connect: Federate identity across your organization with industry-standard protocols, enabling single sign-on (SSO) while maintaining security boundaries
Role-Based Access Control (RBAC)
OpenStack's native RBAC capabilities allow you to define granular permissions across projects, domains, and resources. Atmosphere makes it straightforward to implement least-privilege access:
- Separate duties between cloud operators and tenants
- Create custom roles tailored to your organizational structure
- Audit who has access to what—and why
Secure API Endpoints
Every interaction with your cloud happens through APIs. Atmosphere ensures:
- TLS encryption for all API traffic
- Token-based authentication with configurable expiration
- Rate limiting to prevent abuse
- Comprehensive API logging for audit trails
Network Security Groups and Micro-Segmentation
Atmosphere leverages OpenStack Neutron to give you powerful network isolation:
- Define security groups that act as virtual firewalls for instances
- Implement micro-segmentation to isolate workloads from each other
- Control traffic at the port level—not just the network perimeter
- Create network policies that follow workloads, not IP addresses
Encrypted Storage
Data at rest is protected through:
- Ceph storage encryption for block and object storage
- Key management integration for enterprise key lifecycle
- Encrypted volumes that travel with your instances
Practical Steps to Harden Your Cloud Deployment
Implementing zero-trust isn't a single project—it's an ongoing practice. Here's a roadmap:
1. Establish Strong Identity Foundations
- Integrate with your enterprise identity provider via Keycloak, LDAP, or SAML
- Enforce MFA for all administrative access
- Implement SSO to reduce password fatigue (and the risky behaviors it causes)
2. Audit and Minimize Permissions
- Review existing roles and permissions—remove any that aren't actively needed
- Implement just-in-time access for privileged operations
- Use OpenStack's policy files to customize RBAC for your requirements
3. Segment Your Networks
- Design network topology with isolation in mind
- Use security groups to create micro-perimeters around workloads
- Separate management, storage, and tenant traffic onto distinct networks
4. Enable Comprehensive Logging
- Aggregate logs from all OpenStack services
- Monitor authentication events for anomalies
- Set up alerts for privilege escalation attempts or unusual API patterns
5. Automate Security Compliance
- Use infrastructure-as-code to ensure consistent security configurations
- Implement automated scanning for misconfigurations
- Regularly rotate credentials and certificates
6. Plan for Incident Response
- Assume breach will happen—have playbooks ready
- Design architecture to contain lateral movement
- Test your response procedures regularly
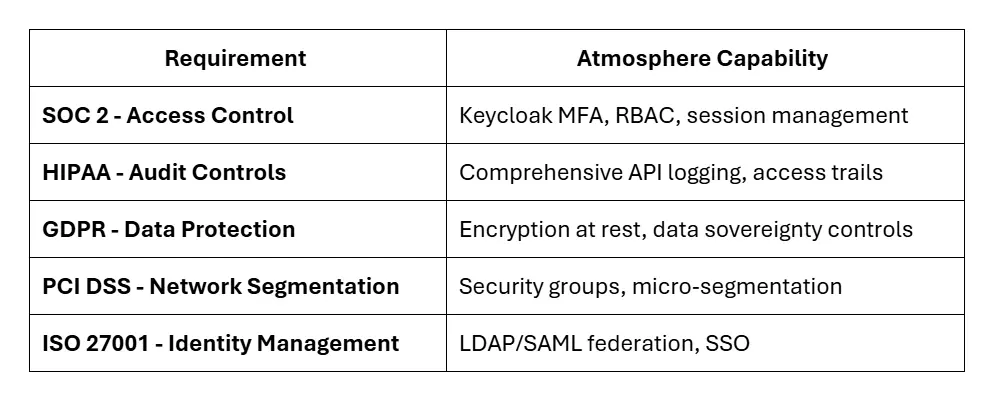
Meeting Compliance Requirements
Zero-trust architecture isn't just good security practice—it's increasingly a compliance requirement. Atmosphere's security features map directly to common frameworks:
The Path Forward
Security-by-default isn't about adding more tools—it's about building infrastructure where security is inherent, not incidental. With OpenStack's transparency and Atmosphere's integrated security capabilities, you can implement genuine zero-trust architecture without sacrificing operational efficiency.
At VEXXHOST, we're continuing to invest in advanced security tooling throughout 2026. Our goal is simple: make robust security the path of least resistance for your cloud deployment.
Ready to build zero-trust cloud infrastructure? Contact our team to learn how Atmosphere can help you implement security-by-default—or explore our security features in depth.