HTTPS is a great way to protect the Apache webserver. HTTPS protects your communication between your browsers and servers from being intercepted or tampered with. Modern browsers will warn you if you use the plain HTTP protocol. Google will show a warning sign if you do not use SSL to serve your content and flag your website as unsafe.
This article will show you how to secure Apache using Let’s Encrypt. Let’s Encrypt is an Internet Security Research Group (ISRG) free certificate authority. Let’s Encrypt offers two types of certificates. There are two types of certificates: the Wildcard SSL (which covers all subdomains as well as a single domain) and the standard single domain SSL. Certbot is a software client that automates most, if not all, of the steps. Let’s Encrypt automates the process by using an algorithm called Automated Certificate Management Environment. Using Let’s Encrypt you can always automate all the processes that are involved in providing proof-of-control for websites, such as renewing, revoking, and obtaining certificates. Any site can enable HTTPS security with a single click or command method.
Prerequisites
Below are the prerequisites to follow all the steps for this article:
- One Ubuntu 20.04 server was installed.
- Logged in as root user or user with Sudo privileges.
- An SSL certificate can only be obtained by a fully registered domain name. It must point to your public IP. This article will be based on demo.com.
Step 1: Install Apache2 Web Server
Apache is included in Ubuntu’s default software repositories. Start by updating your local package. Since we require a web server to install the Let’s Encrypt SSL certificate, I will be installing Apache2.
ubuntu@ubunu2004:~$ sudo apt update
Install the apache2 package using below command.
ubuntu@ubunu2004:~$ sudo apt install apache2
Below are the commands to enable or start the webserver.
ubuntu@ubunu2004:~$ sudo systemctl start apache2.service
ubuntu@ubunu2004:~$ sudo systemctl enable apache2.service
Now Check the status to see if apache service is running properly.
ubuntu@ubunu2004:~$ sudo systemctl status apache2.service
Step 2: Installing Certbot
We will first install Certbot. This is a command-line utility that allows us to obtain the certificate. It allows you to renew and obtain the SSL certificate whenever needed. It can be found in the official Ubuntu APT package repository.
Certbot is part EFF’s efforts to encrypt all of the Internet. Certbot and Let’s Encrypt are able to automate the process and allow you to turn on HTTPS and manage it with simple commands. Certbot and Let’s Encrypt are free to use, so you don’t need to make arrangements for payment. Certbot can be used as a client for Let’s Encrypt CA. It is fully featured and extensible. This client is compatible with UNIX-based operating system.
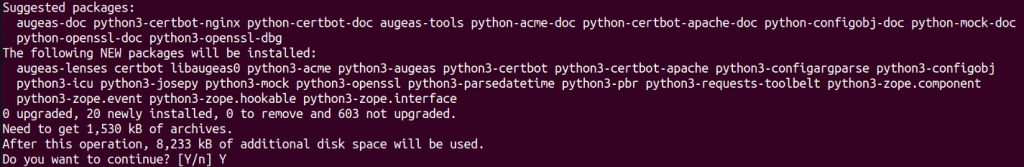
Start the installation process of Certbot and python3-certbot-apache, using the command given below.
ubuntu@ubunu2004:~$ sudo apt install certbot python3-certbot-apache
Step 3: Checking your Apache Virtual Host Configuration
Certbot will need to locate the correct virtualhost in your Apache configuration files.
Virtualhosts are a type hosting provider that specializes in virtual infrastructure solutions. This includes virtual servers, storage, and hybrid platforms that allow data, applications, and/or services to be hosted. It encompasses all technologies and service models that enable individuals and businesses to access computing infrastructure solutions and services via the Internet.
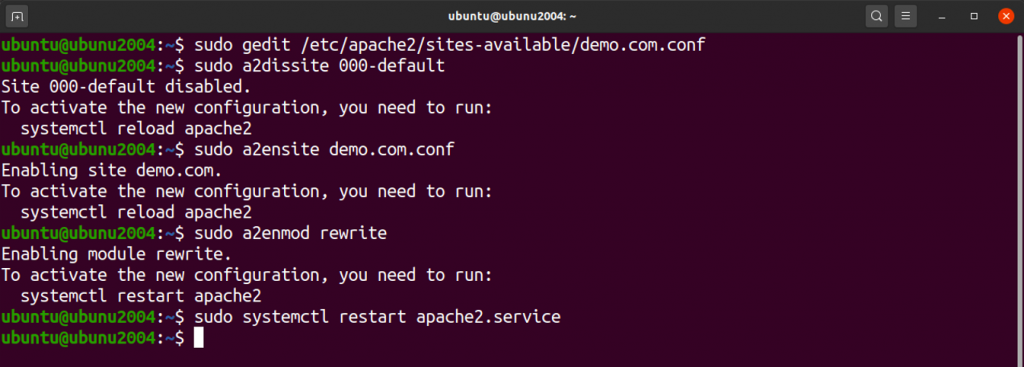
Create a virtualhost for your domain. Use gedit to edit the file demo.com.conf
ubuntu@ubunu2004:~$ sudo gedit /etc/apache2/sites-available/demo.com.conf
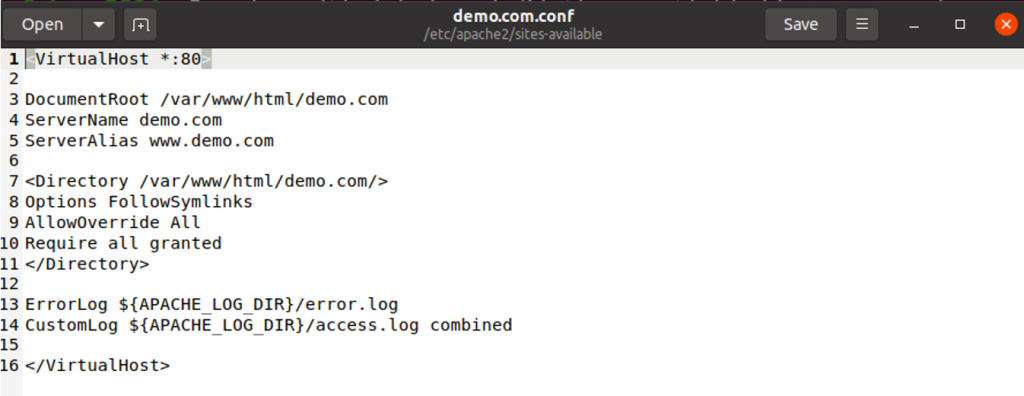
Copy the following configuration into the file. Replace demo.com by your domain name.
<VirtualHost *:80>
DocumentRoot /var/www/html/demo.com
ServerName demo.com
ServerAlias www.demo.com
<Directory /var/www/html/demo/>
Options FollowSymlinks
AllowOverride All
Require all granted
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
Save the file after you are done editing it and close it.
Use the below command to disable default virtualhost.
ubuntu@ubunu2004:~$ sudo a2dissite 000-default
Use the below command to enable the new virtualhost.
ubuntu@ubunu2004:~$ sudo a2ensite demo.com.conf
Use the below command to enable the rewrite.
ubuntu@ubunu2004:~$ sudo a2enmod rewrite
Restart apache web server to allow all changes to take place.
ubuntu@ubunu2004:~$ sudo systemctl restart apache2.service
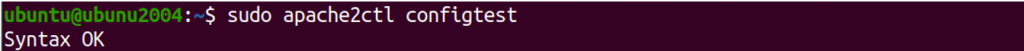
Finally, run the below command to validate all the changes.
Step 4: Allowing HTTPS Through the Firewall
If you have firewall enabled, you need to run below command to allow the “Apache Full” profile and delete the redundant “Apache” profile
ubuntu@ubunu2004:~$ sudo ufw allow ‘Apache Full’
ubuntu@ubunu2004:~$ sudo ufw delete allow ‘Apache’
ubuntu@ubunu2004:~$ sudo ufw status
Finally, now we can run certbot to obtain certificate.
Step 5: Obtaining an SSL Certificate
The following command will get you an SSL certificate with Certbot. After running the certbot command you will first be asked for your email id.
ubuntu@ubunu2004:~$ sudo certbot –apache
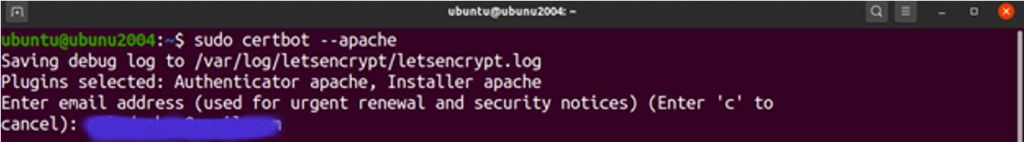
Next, you need to agree to the terms of service by typing A and enter.
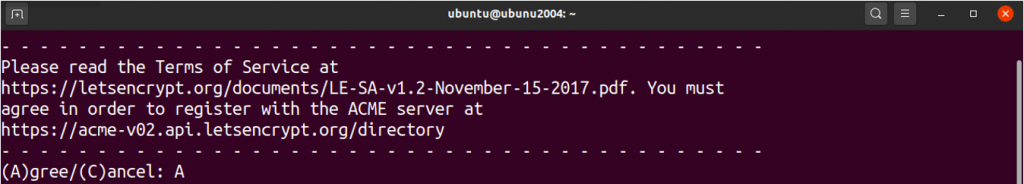
It will then ask you to share your email address with EFF (Electronic Frontier Foundation). Type Y if it is necessary or N if not.
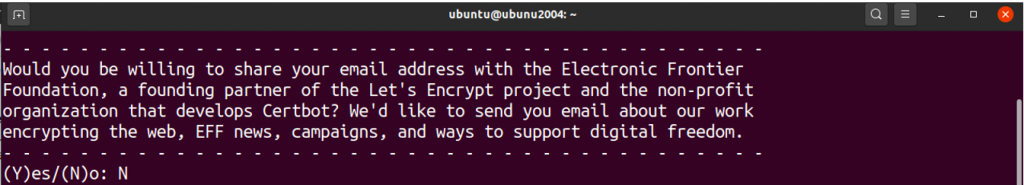
Then, select the domain name which you would like to activate for HTTPS.
Finally, you will get the output like this where a certificate is getting generated.
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for demo.com
http-01 challenge for www.demo.com
Enabled Apache rewrite module
Waiting for verification…
Cleaning up challenges
Created an SSL vhost at /etc/apache2/sites-available/demo.com.conf
Enabled Apache socache_shmcb module
Enabled Apache ssl module
Deploying Certificate to VirtualHost /etc/apache2/sites-available/demo.com.conf
Enabling available site: /etc/apache2/sites-available/demo.com.conf
Deploying Certificate to VirtualHost /etc/apache2/sites-available/demo.com.conf
Next, you will be asked to choose whether you want HTTP traffic to redirect to HTTPS. Enter 1 to disable redirection and 2 for redirection. This was the final step. If you did everything correctly, you will receive a message of congratulations.
Congratulations! You have successfully enabled https://demo.com and https://www.demo.com
Now your certificate has been installed and loaded into Apache. Reload your site using https:// to see your browser’s security indicator. Your site should be properly secured.
Step 6: Verifying Certbot Auto-Renewal
Let’s Encrypt certificates are valid for only ninety days. Installing Certbot will create a cronjob to renew any SSL certificate. You can run the command to check the status of the service.
ubuntu@ubunu2004:~$ sudo systemctl status certbot.timer
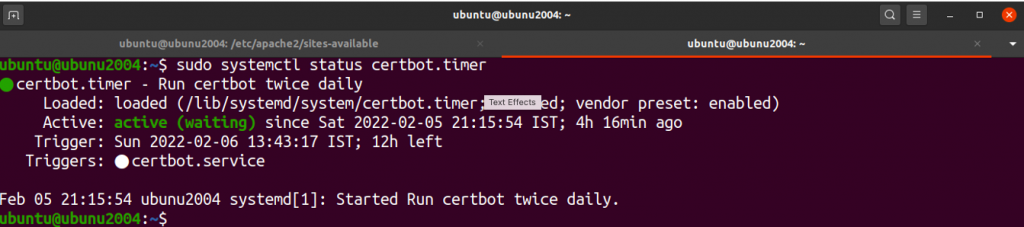
This command can be used to test the automatic renewal of your certificates.
ubuntu@ubunu2004:~$ sudo certbot renew –dry-run
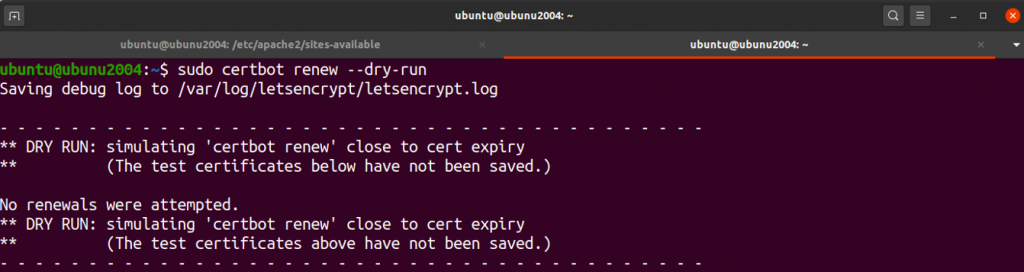
If you see no errors, you’re all set. Certbot can renew your certificates and reload Apache if necessary to take over the changes.
Conclusion
Congratulations! You have successfully installed the Let’s Encrypt SSL certificate on your domain.
This article will show you how to install Certbot and Apache2 web servers, how to create an Apache Virtual Host and how to install an SSL certificate on your domain. Your website should now be secured and will automatically renew to keep it that way.


